NETWORK SECURITY CONTROLS
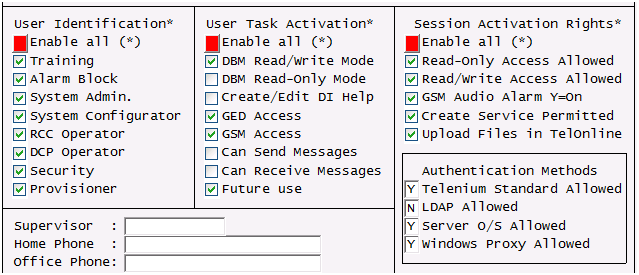
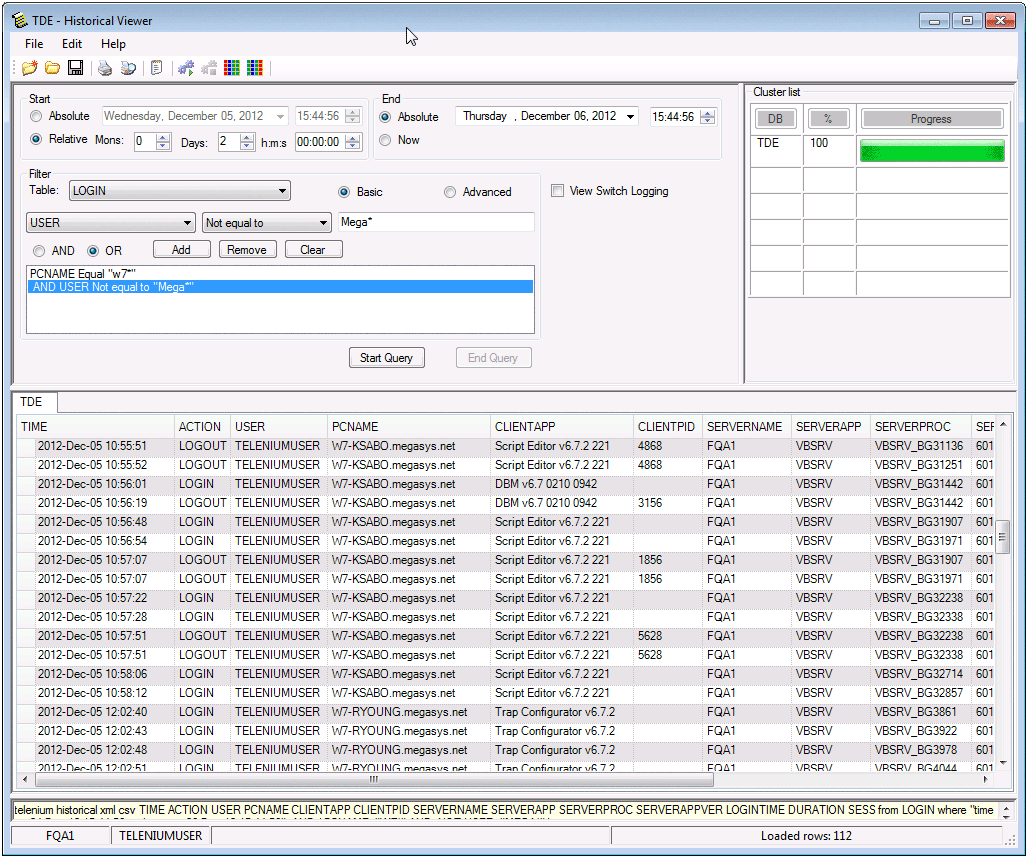
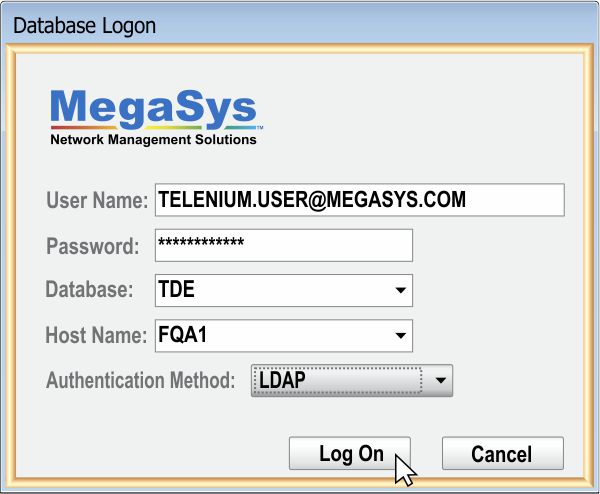
We understand that the integrity of your network should never be compromised. This is why Telenium® utilizes a variety of network security controls features in order protect your network from intentional and unintentional tampering.